Coalition Control
A cybersecurity platform providing real-time risk assessments, threat monitoring, and security tools to help businesses proactively defend against cyber threats and vulnerabilities.
Security
B2B
SaaS
User Research
Personas
User Testing
Info Architecture
Prototypes
Interaction design
Visual design

I
Overview.
Coalition Control serves as the central hub for all Coalition policyholders and technology customers, merging insurance, technology, and services from Coalition and its partners into a seamless, dynamic online experience. This cyber risk management platform is designed to proactively detect, assess, and mitigate cyber risks. By simply providing a business email address, users can quickly create an account. Coalition Control's technology then scans your domain, identifies potential vulnerabilities, and offers actionable recommendations to address any cybersecurity risks uncovered.
II
Dashboard Design.
Powered by Coalition's proprietary technology, claims data, and public information, each company receives a risk score that indicates whether it is at high, medium, or low risk based on the number and criticality of active security findings. This score provides executives and security professionals with a quantitative summary of their overall cybersecurity posture, which evolves as new security findings are discovered and older risks are remediated.
The risk profile also displays the trend of the risk score over time, helping to visualize how the security posture is progressing. It highlights the count, severity, and trend of security findings that contribute to the risk score, along with a snapshot of the company's assets.
During the policyholder's policy period, scan details don’t alter current insurance terms. However, unresolved issues could lead to complications at renewal and impact claims. To mitigate cyber risk, Coalition provides alerts on vulnerabilities from an external perspective, based on security best practices. These alerts may vary from initial risk assessments due to the evolving threat landscape. Coalition ensures policyholders receive an updated view of active risks to help prepare for insurance renewal. User flows were designed to integrate the resolution process with the scanning experience, balancing user needs with the technical aspects. Prototypes were tested with real policyholders to confirm they met their needs effectively.
To keep users informed of new findings, they receive alerts through dashboard notifications and email alerts. Users can choose to resolve either the entire security finding group or individual security findings. For critical findings, users select the method used to fix the issue and then click "Resolve." If the finding is scannable, resolution success will be confirmed within 1 business day, and users will receive an email notification. For findings where resolution cannot be confirmed through compensating controls like MFA, users can attest to a compensating control. The security support team will review these requests and notify users of the resolution status. The Risk Score and Scan History will be updated accordingly, and critical resolution requests can be tracked in the Critical Resolution Request Log.
UX Flows
The Security Checklist guides SME and mid-market companies through a simple, step-by-step process to improve their cybersecurity. Based on CISA and CIS controls, each task includes guidelines, reference links, and recommended vendors to assist completion. Users can easily attest to completed tasks, progressing through security statuses (Standard, Strong, Best-in-Class). Higher statuses enhance protection and may qualify the company for a premium discount at renewal. The design focuses on clarity, ease of use, and actionable insights, making it accessible even for users with limited technical expertise.

.png)
.png)
.png)
III
Report Templatization.
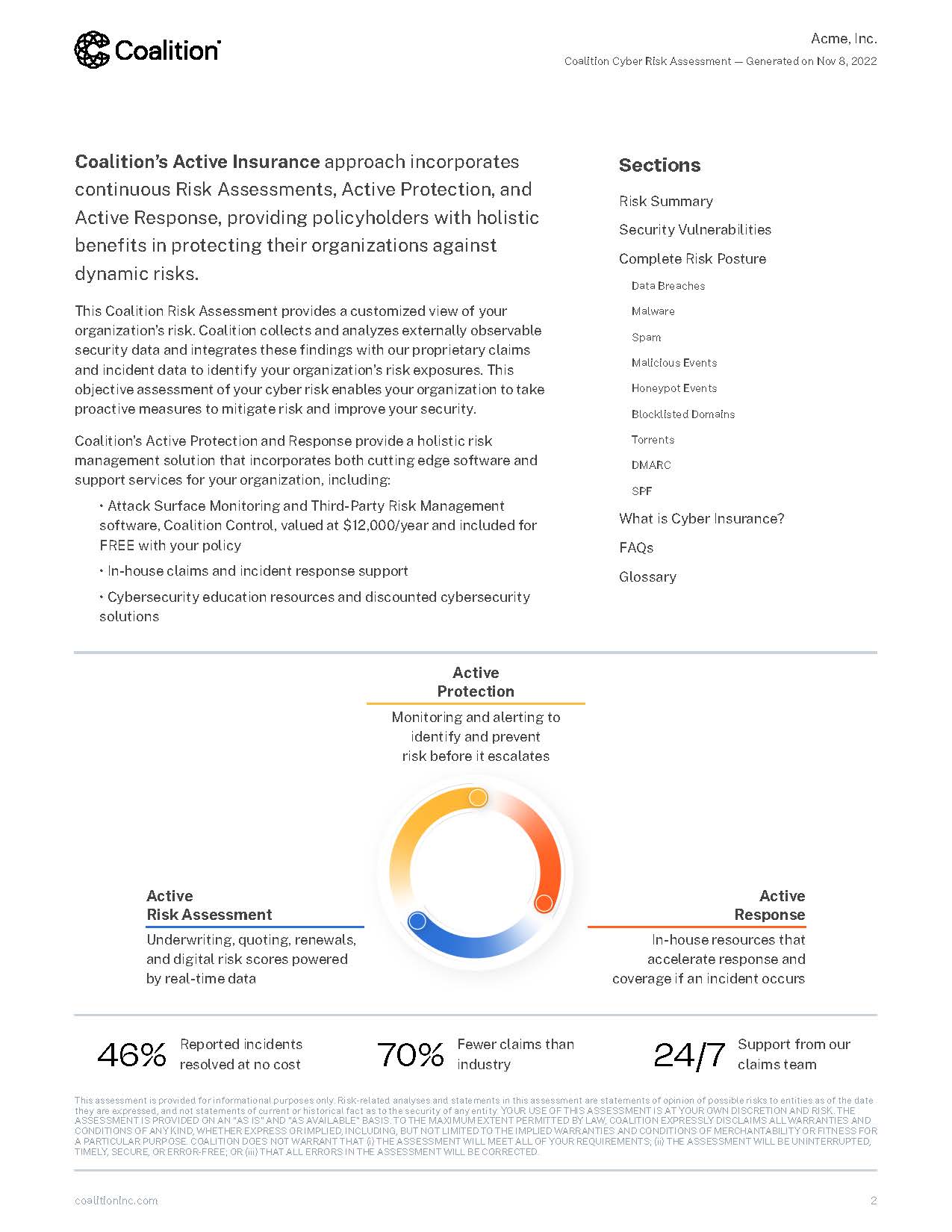
The Coalition Risk Assessment (CRA) is a detailed report that provides an evolving overview of a company's risk profile, updating in real-time to ensure users have access to the latest insights. I designed the PDF version of the CRA using modular components and templates to create a consistent and easily customizable format. User feedback played a crucial role in guiding the taxonomy and prioritization of content for various user personas, ensuring that the report addresses the specific needs of different audiences.
I collaborated with developers using the PDF Generator API to integrate these modular components seamlessly. This approach allows users to download the report on demand within Coalition Control and share it effortlessly across teams and stakeholders. The modular design ensures that the report is both visually cohesive and adaptable, supporting efficient distribution, collaboration, and informed decision-making across any device.
Cover

Page 2
Page 3

Page 4

Page 5

Page 7

Page 10

Page 11

Page 16

Page 21
